Give Invictus access to your Azure Active Directory
To use your Azure Active Directory groups as a way of authentication and flow authorization, you need to follow these steps.
Register an Application for Invictus
Expose an API with scoped permissions
Add API permissions
Pass App Registration values to Invictus deployment
Sync your Azure Active Directory groups to Invictus Only Admins
Groups available in your Azure Active Directory will be used to determine whether users can access certain flows in the Invictus Dashboard. (See flow permissions).
warning
Only groups of active users (Active Directory users that have already signed into the Dashboard) will be synced within the Dashboard.
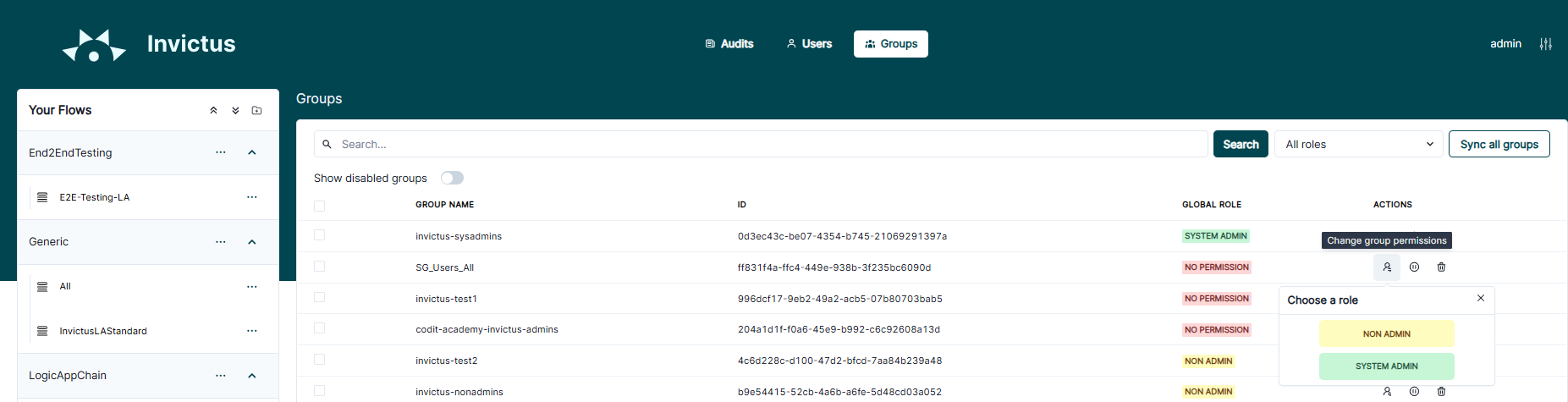
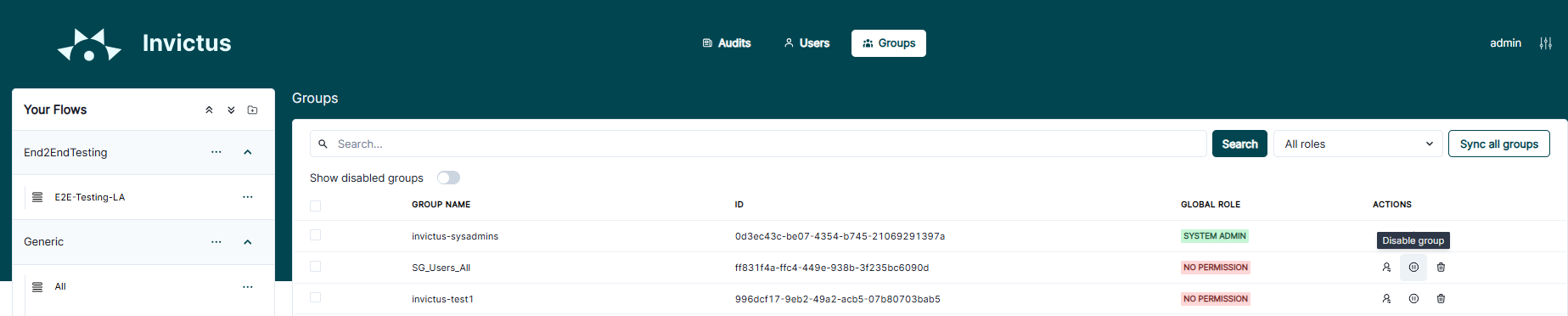
Enable only required groups Only Admins
Once the groups are synced within the Dashboard, you have to manually enable the required groups which you want to use for flow permissions.
Assign user role to required groups Only Admins
Each enabled group requires a user role permission to indicate what authority each member of the group has throughout the Dashboard, more info on Dashboard roles.